Google Apps for Education
Overview
This will describe how to get Shibboleth 3.4.x working with Google Apps for Education
Shibboleth IDP Configuration
In the code below:
Replace university.edu which your Google Domain.
----------
relying-party.xml
Find the section that says
<util:list id="shibboleth.RelyingPartyOverrides"> . . . </util:list>
And add in between:
<bean parent="RelyingPartyByName" c:relyingPartyIds="google.com/a/university.edu">
<property name="profileConfigurations">
<list>
<bean parent="SAML2.SSO" p:encryptAssertions="false" />
</list>
</property>
</bean>
The above turns off encrypted assertions which Google does not support.
Create your google-university-metadata.xml, it should look like this:
<EntityDescriptor entityID="google.com/a/university.edu" xmlns="urn:oasis:names:tc:SAML:2.0:metadata">
<SPSSODescriptor protocolSupportEnumeration="urn:oasis:names:tc:SAML:2.0:protocol">
<NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress</NameIDFormat>
<AssertionConsumerService index="1" Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST"
Location="https://www.google.com/a/university.edu/acs" />
</SPSSODescriptor>
</EntityDescriptor>
In your metadata-providers.xml file add the following:
<MetadataProvider id="Google” xsi:type="FilesystemMetadataProvider" metadataFile="%{idp.home}/metadata/google-university-metadata.xml"/>
In your attribute-resolver.xml, add the following:
<AttributeDefinition xsi:type="Simple" id="mail">
<InputDataConnector ref="myLDAP" attributeNames="mail"/>
<AttributeEncoder xsi:type="SAML1String" name="urn:mace:dir:attribute-def:mail" encodeType="false" />
<AttributeEncoder xsi:type="SAML2String" name="urn:oid:0.9.2342.19200300.100.1.3" friendlyName="mail" encodeType="false" />
</AttributeDefinition>
This is of course, if you have your email address stored in the mail attribute in LDAP.
For instance, mine would be melvin.lasky@university.edu
In your attribute-filter.xml, add the following:
<!-- G Suite (Google Apps) -->
<AttributeFilterPolicy id="google.com/a/university.edu">
<PolicyRequirementRule xsi:type="Requester" value="google.com/a/university.edu" />
<AttributeRule attributeID="mail">
<PermitValueRule xsi:type="ANY" />
</AttributeRule>
</AttributeFilterPolicy>
Note: Google does not appear to care what attribute you send for mail, just ensure it is the same in the saml-nameid.xml.
And lastly, in your saml-nameid.xml, uncomment the following beans (they are commented out by default):
.
.
.
<bean parent="shibboleth.SAML2AttributeSourcedGenerator"
p:omitQualifiers="true"
p:format="urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress"
p:attributeSourceIds="#{ {'mail'} }" />
.
.
.
<bean parent="shibboleth.SAML1AttributeSourcedGenerator"
p:omitQualifiers="true"
p:format="urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress"
p:attributeSourceIds="#{ {'mail'} }" />
------
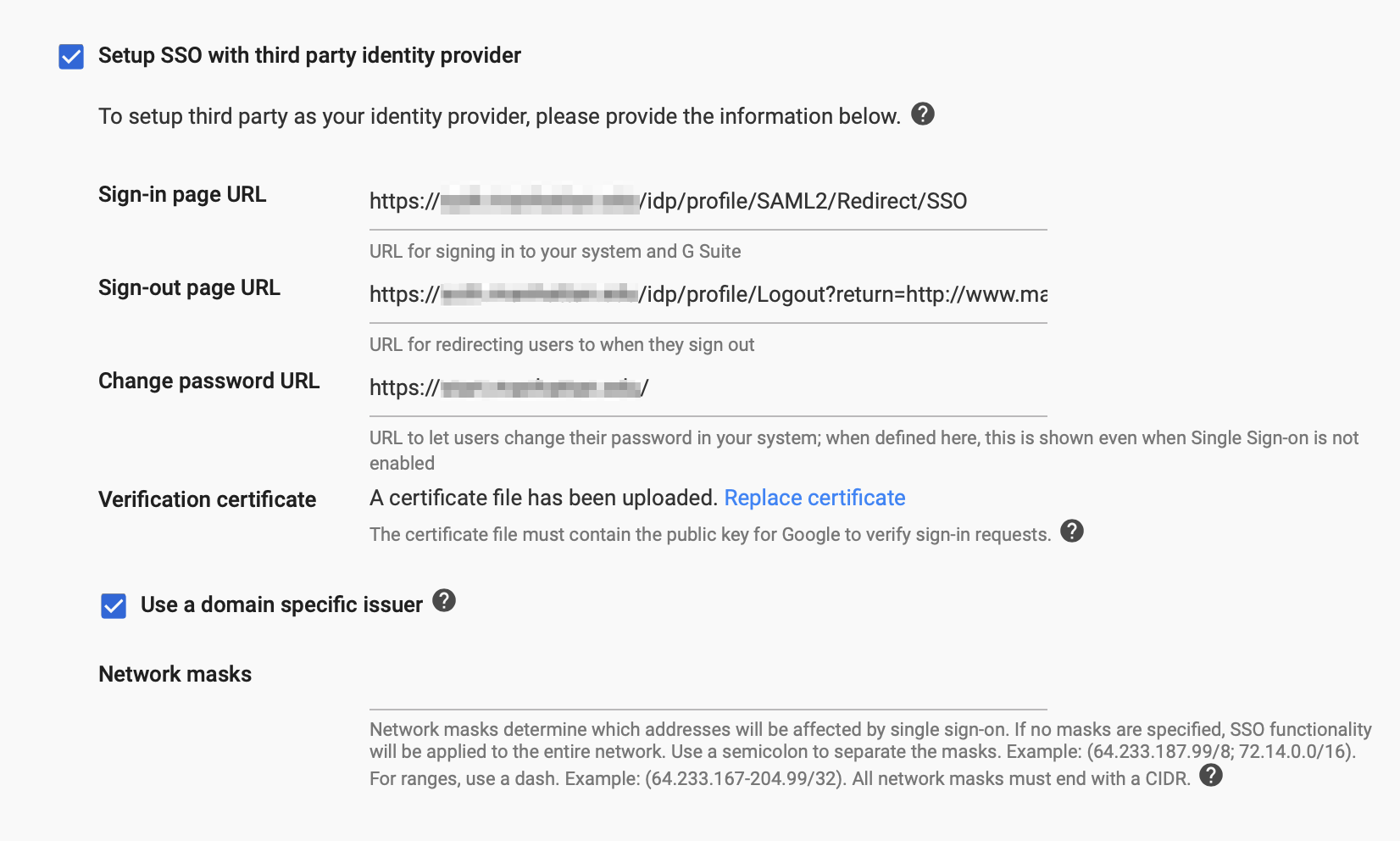
Now, on your Google Apps for Education Admin portal
Sign In Page:
https://shibserver.university.edu/idp/profile/SAML2/Redirect/SSO
Sign Out Page:
https://shibserver.university.edu/idp/profile/Logout
And make sure “Use a domain specific issuer” is checked.
Also, that verification certificate is your idp-signing.crt
That's it. Once you have completed the above, you should have a working Google Apps for Education instance authenticating off of your Shibboleth server.