Slack Enterprise Grid
This guide will describe how to get Shibboleth 3.2.x working with Slack Enterprise Grid. Currently the vendor does not have documentation on this integration for Shibboleth IDPs, here is how I got it working. Note, you must configure your IDP before working within the Slack Enterprise Grid SSO configuration as part of the configuration is to test your IDP; hence you need these settings in your IDP before testing.
This is not a replacement for the actual documentation and you cannot cut and paste your way to a working system. The examples are not usable without taking into consideration your local needs and requirements.
Shibboleth IDP Configuration
Slack Enterprise Grid does not provide you with a metadata file, so you need to create one. You get to name the SP's entity ID, their recommendation is https://slack.com.
Metadata-file.xml
<?xml version="1.0"?> <md:EntityDescriptor xmlns:md="urn:oasis:names:tc:SAML:2.0:metadata" entityID="Entity ID Goes Here"> <md:SPSSODescriptor protocolSupportEnumeration="urn:oasis:names:tc:SAML:2.0:protocol" AuthnRequestsSigned="false" WantAssertionsSigned="true"> <NameIDFormat>urn:oasis:names:tc:SAML:2.0:nameid-format:persistent</NameIDFormat> <md:AssertionConsumerService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://YourGridURL.enterprise.slack.com/sso/saml" isDefault="true" index="0"/> </md:SPSSODescriptor> </md:EntityDescriptor>
Attribute-resolver.xml
We had to create two additional attribute resolver entries, one for User.Email (required) and User.Username (not required)
<resolver:AttributeDefinition xsi:type="ad:Simple" id="User.Username" sourceAttributeID="uid">
<resolver:Dependency ref="myLDAP" />
<resolver:AttributeEncoder xsi:type="enc:SAML2String" name="User.Username" friendlyName="User.Username"/>
</resolver:AttributeDefinition>
<resolver:AttributeDefinition xsi:type="ad:Simple" id="User.Email" sourceAttributeID="userprincipalname">
<resolver:Dependency ref="myLDAP" />
<resolver:AttributeEncoder xsi:type="SAML2String"
xmlns="urn:mace:shibboleth:2.0:attribute:encoder"
name="User.Email" friendlyName="User.Email"/>
</resolver:AttributeDefinition>
Attribute-filter.xml
Per the documentation, you can also send the optional attributes of first_name and last_name.
<AttributeFilterPolicy id="YourGridURL.enterprise.slack.com">
<PolicyRequirementRule xsi:type="Requester" value="https://YourGridURL.enterprise.slack.com" />
<AttributeRule attributeID="first_name">
<PermitValueRule xsi:type="ANY" />
</AttributeRule>
<AttributeRule attributeID="last_name">
<PermitValueRule xsi:type="ANY" />
</AttributeRule>
<AttributeRule attributeID="User.Email">
<PermitValueRule xsi:type="ANY" />
</AttributeRule>
<AttributeRule attributeID="User.Username">
<PermitValueRule xsi:type="ANY" />
</AttributeRule>
<AttributeRule attributeID="universityid"><--This is used within saml-nameid.xml -->
<PermitValueRule xsi:type="ANY" />
</AttributeRule>
</AttributeFilterPolicy>
Relying-party.xml
<bean parent="RelyingPartyByName"
c:relyingPartyIds="https://YourGridURL.enterprise.slack.com">
<property name="profileConfigurations">
<list>
<bean parent="SAML2.SSO"
p:signAssertions="true"
p:signResponses="true"
p:encryptAssertions="false"
p:encryptNameIDs="false"
/>
</list>
</property>
</bean>
Saml-nameid.xml
<bean parent="shibboleth.SAML2AttributeSourcedGenerator"
p:format="urn:oasis:names:tc:SAML:2.0:nameid-format:persistent"
p:attributeSourceIds="#{ {'universityid'} }" >
<property name="activationCondition">
<bean parent="shibboleth.Conditions.RelyingPartyId" c:candidate="https://YourGridURL.enterprise.slack.com" />
</property>
</bean>
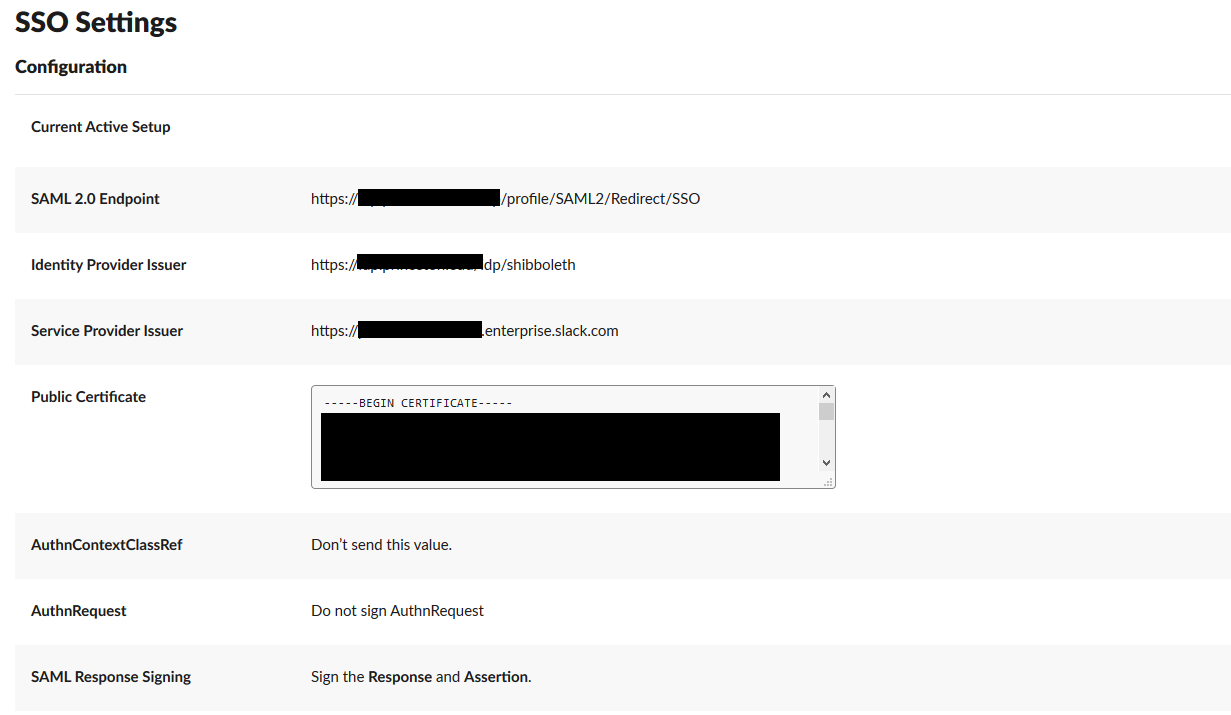
Slack Enterprise Grid Configuration
Once you have configured your IDP, you can now configure Slack Enterprise Grid. Login as a Grid owner and head to the SSO configuration page.